       |
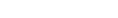
|
RSA is a public key encryption algorithm that uses separate keys for encryption and decryption. You may want to use RSA key exchange if your organization stores sensitive information in Surround SCM and users access the Surround SCM Server using a username and password in client applications outside of your network.
If you use RSA key exchange, a public key fingerprint must be imported to all client applications that connect to the Surround SCM Server.
1. Choose Tools > Administration > Server Options.
The Server Options dialog box opens with the General category selected.
2. Select Encrypt communication between clients and the server and Use RSA key exchange.
A public key is generated on the Surround SCM Server. The Fingerprint field displays the public key fingerprint, which is a short version of the public key. Public and private keys are stored in the rsakeys directory in the Surround SCM application directory on the Surround SCM Server computer.
Note: If you clear the Use RSA key exchange option, you are prompted that all users will need to modify their server settings. Click Yes if you no longer want to use RSA. Make sure the public key fingerprint is removed from server connection settings in Surround SCM clients and server settings in the Surround SCM Registry Utility for web and proxy servers.
3. Click Download Public Key to save an XML file that contains the Surround SCM Server address, port number, and public key fingerprint.
This file must be imported to Surround SCM clients that connect to the server. Make sure the file is securely stored and distributed to users for import. If a hacker has unauthorized access to the file, changes it, and it is imported to clients, your Surround SCM installation could be hacked.
Note: The server address in the XML file includes the default hostname of the Surround SCM Server computer. If users connect to the server from outside the local network, you must manually update the server address in the server settings file before providing it to users.
4. Click OK to save the changes.
5. Import the server settings file to Surround SCM clients that connect to the server.
Tip: If you suspect the private key on the Surround SCM Server was compromised because of unauthorized server access, regenerate the public and private key pair. Click Regenerate Key Pair and click OK when you are prompted to generate the new keys. If you regenerate the keys, you must download a new server settings file and update all client applications that connect to the server.