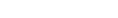Security groups control user access to Surround SCM actions. A user only has access to perform actions based on the enabled commands for the security group they are assigned to. Carefully consider the Surround SCM access users in different roles need and set up security groups accordingly to avoid security issues.
When creating security groups, only enable commands for the actions you want users in the group to access. This reduces the potential for users to accidentally modify data or settings they should not have access to.
Security levels
Surround SCM has server, repository, and branch security. The different levels give you granular control over individual branches and repositories and let you configure more complex security scenarios when needed.
- Server security restricts actions users can perform in all branches and repositories, and controls access to general actions, administrative actions, user and security group management, and file and branch actions.
- Repository security restricts the file-related actions users can perform in specific repositories across all branches. If repository security is configured for a security group, users in the group can only perform actions enabled for the specified repositories.
- Branch security restricts the file-related actions users can perform in specific repositories in specific branches. If branch security is configured for a security group, users can only perform actions enabled for the specific branches. Branch security is generally used to give a security group access to a specific branch while maintaining the repository security settings in other branches.
Most organizations only need to configure server security based on user roles to provide access to specific actions in all branches and repositories. You can also override security for specific repositories and branches to restrict users who can access them and the actions they can perform.
How security is applied
By default, Surround SCM security is restrictive, or pessimistic, which means no commands are enabled when you create a new security group and users can only perform actions if the corresponding command is enabled. For example, new users cannot log in to the Surround SCM Client unless they are added to a group with the Login Via GUI Client command enabled. Users can be in multiple groups. If a command is enabled in at least one group a user is in, they can perform the action.
Repository or branch security can override server security file permissions. For example, users in the Developers group can destroy files because the Destroy File command is enabled for the group. If security for the Licenses repository is modified and the Destroy File command is not enabled, users in the Developers group cannot destroy files in that repository, but they still can in other repositories because of the default server security. Repository security always overrides server security and branch security always overrides repository and server security.
Repository-level security
To manage a large number of users and projects with minimal administrative effort, consider using the following repository-level security model.
1. Create an All Users security group to allow read-only access to all repositories
Add this security group as a baseline for all users, which you can then build on by creating other groups with more specific security settings and configuring security for specific repositories and branches. Add all new users to this group.
Configure server security for the group. Select all commands in the General category and make sure all commands in the Admin, Users, Security Groups, and Branch categories are cleared. In the Files (Default) category, only select the View Repository List command to allow users to view repositories and files but not perform any actions that require read/write access, such as checking files in and out. The following screenshot shows the enabled commands for the All Users group.
2. Optionally create a Power Users security group
To allow other high-level users, such as managers or team leads, to perform some administrative actions, create a Power Users group. Duplicate the default Admin group, rename the new group, and clear any commands these users do not need. For example, these users may not need to edit server options or analyze, repair, or lock databases.
3. Create a security group for each project repository
When a repository for a new project is created, add a new security group and then add users working on the project to it. Enable the appropriate file commands for the group so they can work with files as needed. If users are not assigned to the group created for a project, they can only view the repository because no other file commands are enabled in the All Users group.
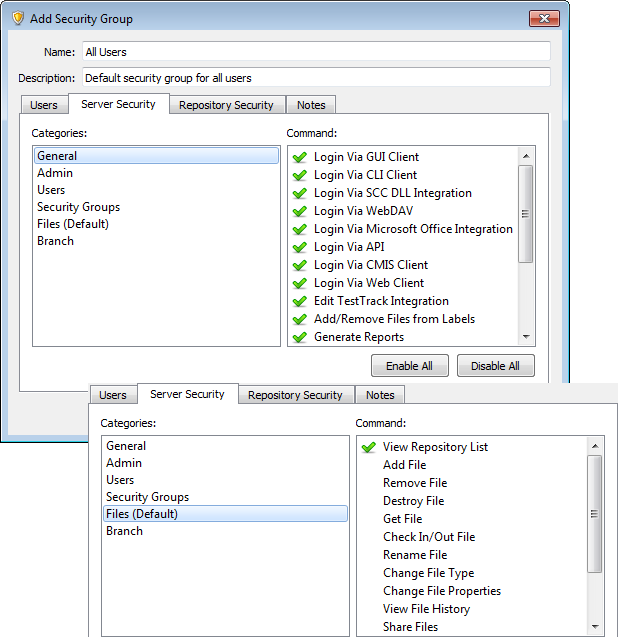
4. Hide repositories from non-project users
If you only want users in a project-based group to see repositories or files, hide repositories so users who are not in the group cannot see them.
To hide a repository, modify its properties and make sure only the group that needs access to it has all or some security enabled. Add <All other groups> to disable all security for all other groups, including any groups created later. The following screenshot shows the security overrides to hide a repository from all groups except the Wysi Developers project group.
Branch-level security
When new branches are created, repository security from the parent branch is inherited and used by default. If you only want a specific group of users to have read/write access to a branch, set the branch to use its own security and add a security group for the branch users.
Only use branch security when you want to provide a group with access to a specific branch while retaining repository security settings in other branches.
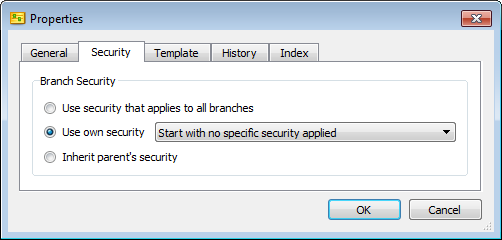
1. Set the branch to start with no specific security applied
Users with access to the repository in the parent branch can access the repository in the new branch. Configuring the branch to use its own security overrides the server and repository security settings to provide access only to users in selected groups.
To set a branch to use its own security, edit the properties to start with no specific security applied.
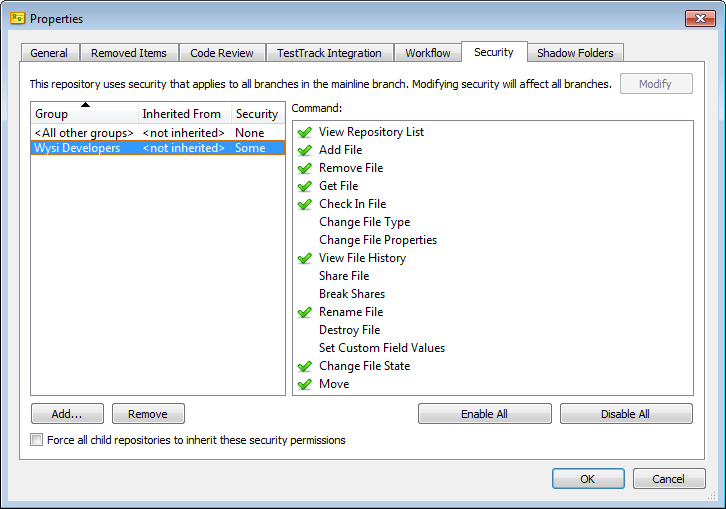
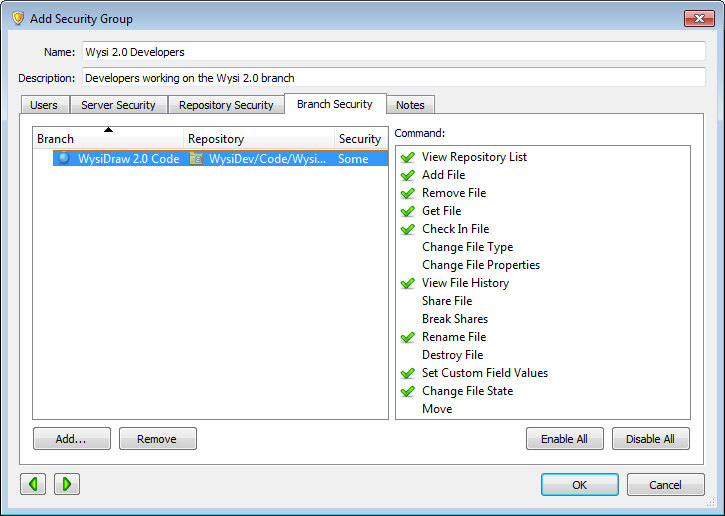
2. Create a branch security group
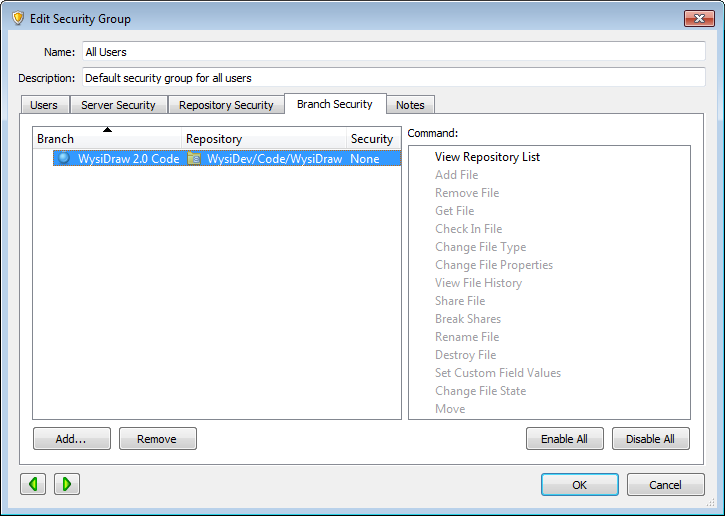
After a branch is set to use its own security, add a security group that only includes users who need to access it. Make sure the branch is added on the Branch Security tab in the group and the commands for the file actions users may perform are selected. The following screenshot shows the Wysi 2.0 Developers group and the enabled commands for the WysiDraw 2.0 Code branch.
3. Override branch security for groups that do not need to access it
If a branch is set to use its own security, repository security inherited from the parent branch is removed and all security groups can view it by default. To hide a branch from a specific security group, edit the group and make sure the branch is added on the Branch Security tab with all commands cleared. The following screenshot shows the All Users group branch security overridden to disable all commands for the WysiDraw 2.0 Code branch. Users in the group cannot access the branch.